A Secret is an object that contains a small amount of sensitive data such as a password, a token, or a key.
In our previous blog, we create a deployment of the PostgreSQL database.
Remember, on that blog we use env in the below format:
env:
- name: POSTGRES_USER
value: postgres
- name: POSTGRES_PASSWORD
value: postgres123
This is not a recommended way to manage the secrets , it can be easily read by anyone.
So there is a solution provided by Kubernetes to manage the secrets like above.
(1) Create a Secret.
The values for all keys in the data the field has to be base64-encoded strings.
to create your secret data into base64 , there are two ways.
On Linux/Mac
echo -n 'dbpassword11' | base64Online tool: https://codebeautify.org/base64-encode
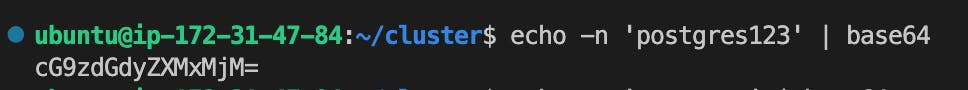
For example in below example we converted secret text postgres123 to base64 text.echo -n 'postgres123' | base64
(2) Create Secrets manifest.
apiVersion: v1
kind: Secret
metadata:
name: postgres-db-envs
type: Opaque
data:
POSTGRES_USER: cG9zdGdyZXM=
POSTGRES_PASSWORD: cG9zdGdyZXMxMjM=
(3) Update Deployment Env configs.
env:
- name: POSTGRES_USER
valueFrom:
secretKeyRef:
name: postgres-db-envs
key: POSTGRES_USER
- name: POSTGRES_PASSWORD
valueFrom:
secretKeyRef:
name: postgres-db-envs
key: POSTGRES_PASSWORD
As you can see in the above file, Because Secrets can be created independently of the Pods that use them, there is less risk of the Secret (and its data) being exposed during the workflow of creating, viewing, and editing Pods. Kubernetes, and applications that run in your cluster, can also take additional precautions with Secrets, such as avoiding writing secret data to nonvolatile storage.
Made with ❤️ by Pratikkumar Panchal. github.com/m3pratik/31daysofEKS
